If you are only as strong as your weakest link, don’t let that weak link be your detection and response capabilities..
There will always be multiple gaps in each layer of your defense in depth model. Make sure finding those gaps takes longer than your detection and response times.
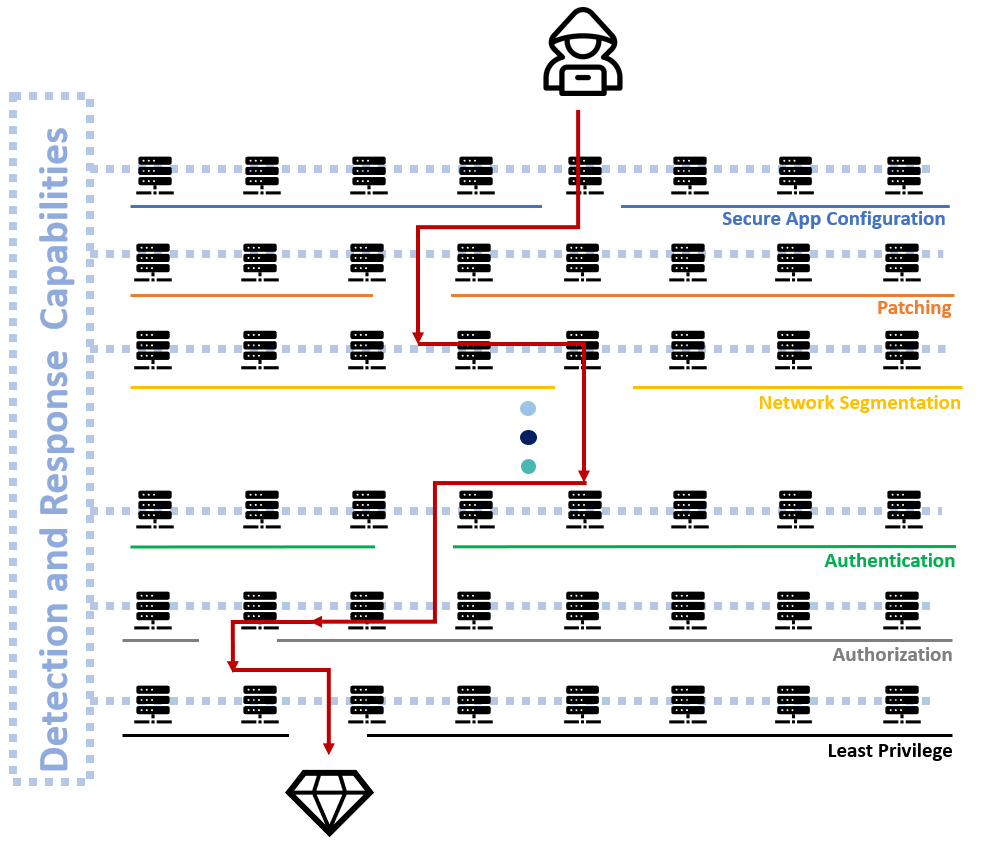
Visualizing attacks with the Attack Kill Chain is helpful, but it doesn’t demonstrate all of the nitty gritty things that an attacker has to bypass in order to execute on their objective. Same goes for public breach data, often times, only the entry point is discussed. It would be more valuable to discuss what could have been done internally to prevent the breach in favor of discussing the perimeter.
The following model isn’t inclusive of all the controls and and layers of the security onion, but it does offer a visualization of how an attacker moves through an environment, its often finding that one weak system out of tens or hundreds of secure systems.